We had a situation where we were calling an external Web service that required custom http headers. When our request reached the Web service the customer http headers had disappeared. We did not know if the problem was with the OSB, our Internet proxy or the programmer 🙂 To find out what was going on I installed the Wireshark sniffer.
Wireshark is part of the standard Red Hat / Oracle Linux Channels so it can most likely be installed directly via yum / up2date.
I installed two packages:
wireshark-gnome-1.0.15-1.el4_8.3 wireshark-1.0.15-1.el4_8.3
The gnome package contains the gui part.
The gui can be started by executing the wireshark command.
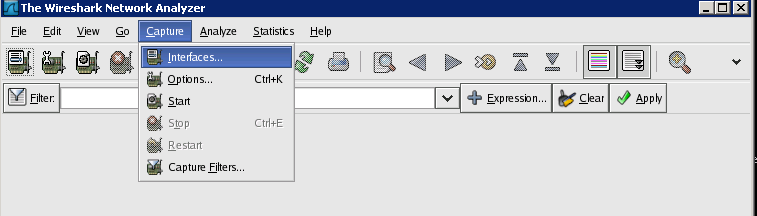
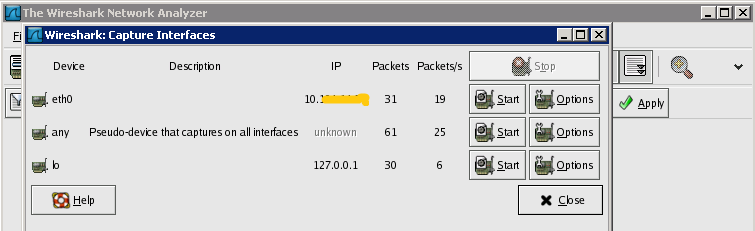
To start capturing packages select Capture and then Interfaces. Select the interface you want to capture traffic from by pressing Start.
If you don’t know which interface then select the first one. There is pseudo interface called any that captures from all interfaces but Wireshark crashed when I tried to use it.
Now execute the program that will generate the communication you want to capture and then press the stop icon.
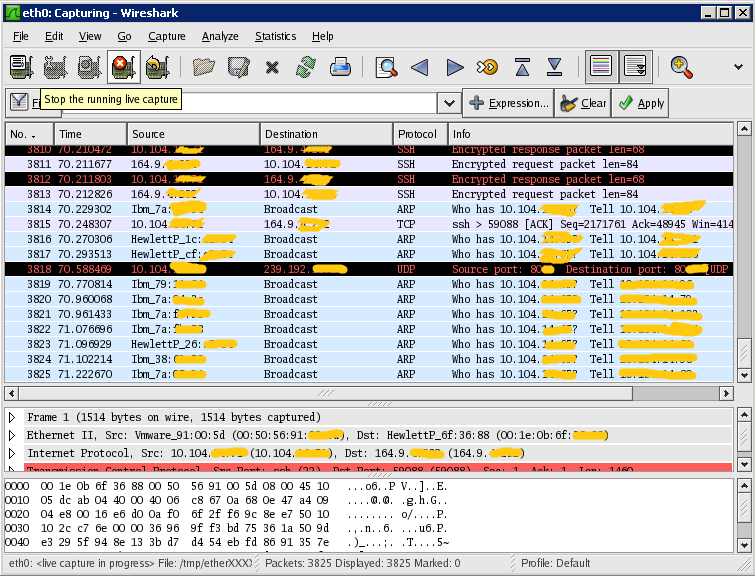
Wireshark have now captured a lot of packages and most of them is probably not interesting, so it is possible to apply a filer.
I wanted only http communication and only calls to our proxy that runs on port 8080:
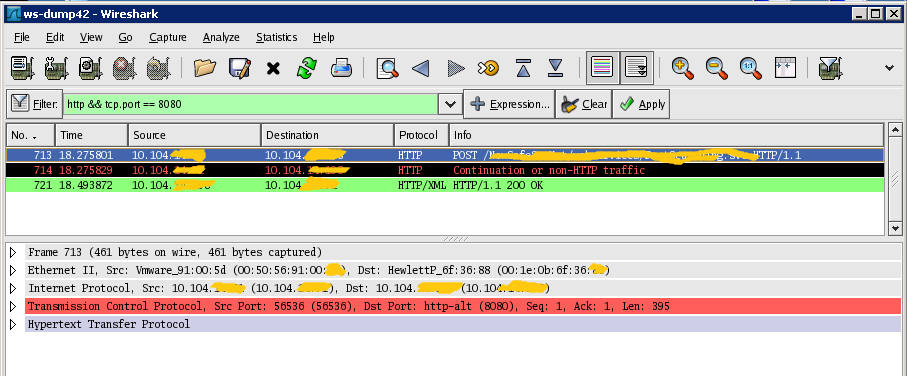
So there are only 3 interesting packages. Now it is possible to drill down in the packages and see the content.
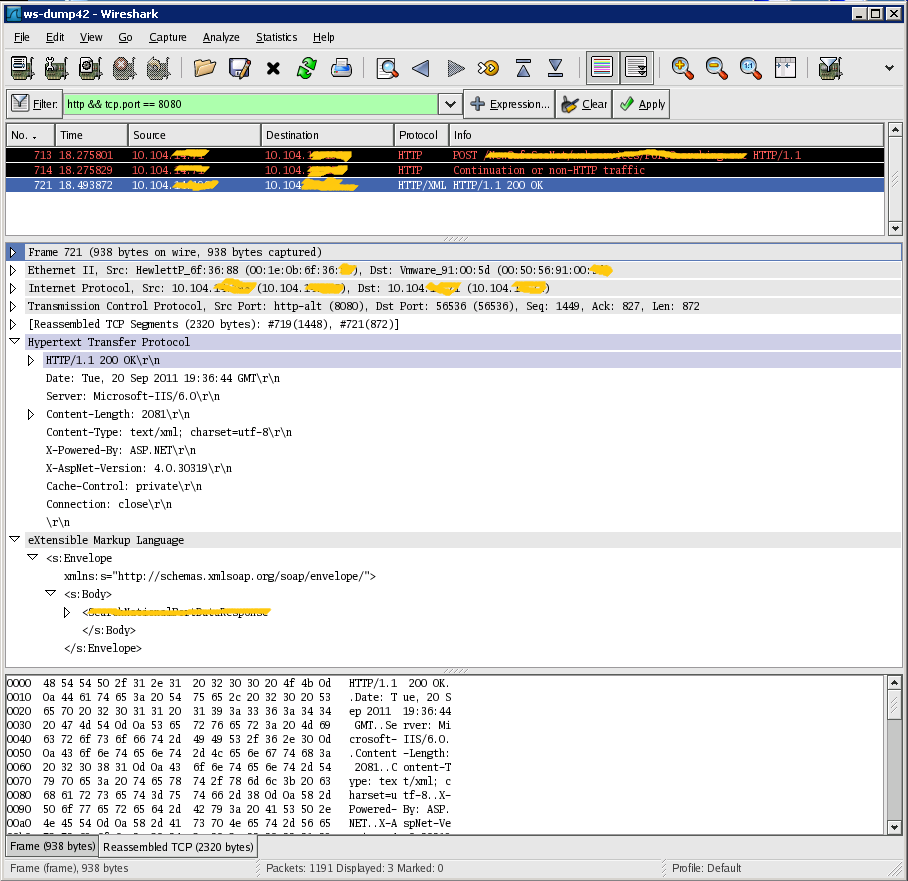
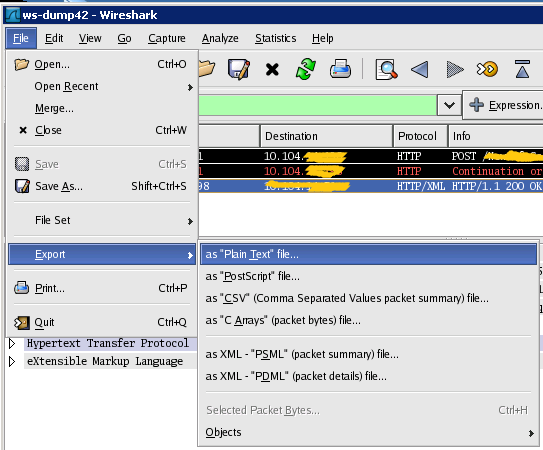
It is possible to export the packages you have filtered to a text file.
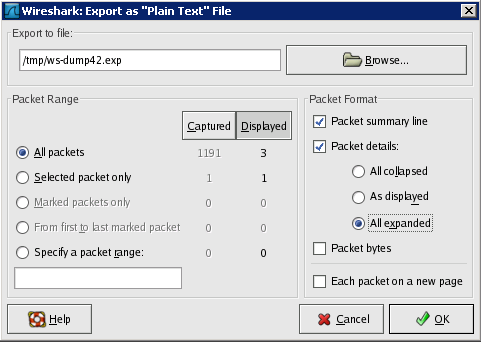
Select Displayed and All packets.
 Twitter
Twitter LinkedIn
LinkedIn GitHub
GitHub GoodReads
GoodReads Last.fm
Last.fm