
I will describe how you create and configure trust stores for the WebLogic Server.
Overview
- Chain of trust
- Keystores
- Creating a Trust Store
- Configure a Trust Store for a Managed Server
- Problems with misconfigured SSL
- Creating an empty Identity Store
Chain of trust
When a SSL server certificate is issued by a CA it is signed by a another certificate. Normally this will be an intermediate certificated, that is again signed by the CAs root certificate. So there is a chain of trust between the SSL server certificate, the intermediate certificate and the root certificate.
When you access a website that uses SSL/TLS to protect the communication between the browser and the site, the chain of trust is evaluated and if it fails, you will get a security warning.
The web server should supply the SSL server certificate and the intermediate certificate. The browser has a build in trust store, that must contain the root certificate.
Here is an example.
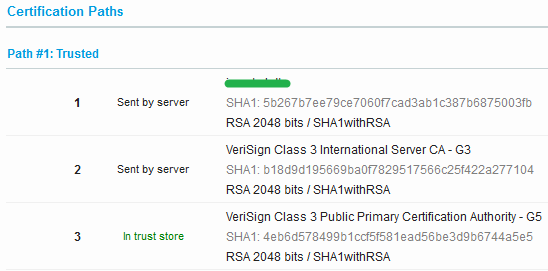
#1 is the SSL server certificate, #2 the intermediate certificate and #3 the root certificate.
Keystores
When a WebLogic server application access a SSL protected site, it must present the root certificate, so the chain of trust can be validated. The certificate is stored in a file called a keystore. A keystore is a secure place to store certificates. It comes in two flavors, trust and identity. A trust store contains certificates that are issued by somebody you trust, like a root certificate from a CA. An identity store contains your own certificates and they are used to authenticate you when you access an external service. A trust store does not contain sensitive information, while identity stores contains very sensitive information like private keys.
Both Java and the WebLogic Server comes with build-in demo keystores. WebLogic is default configured to use them both.
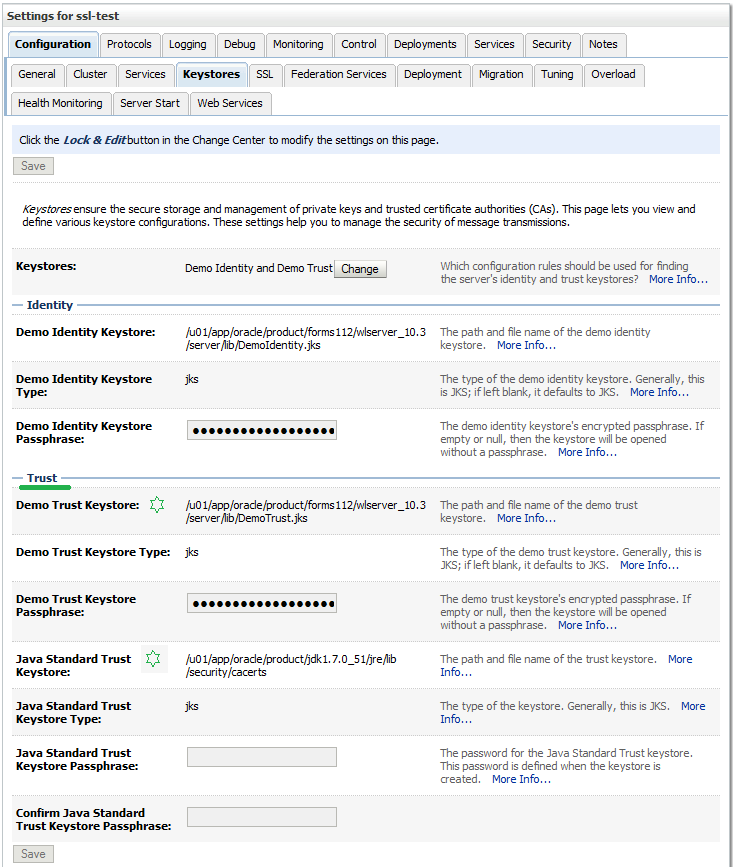
By the way, the default password for the Java cacerts keystore is changeit. The passwords for the WebLogic demo stores can be found here.
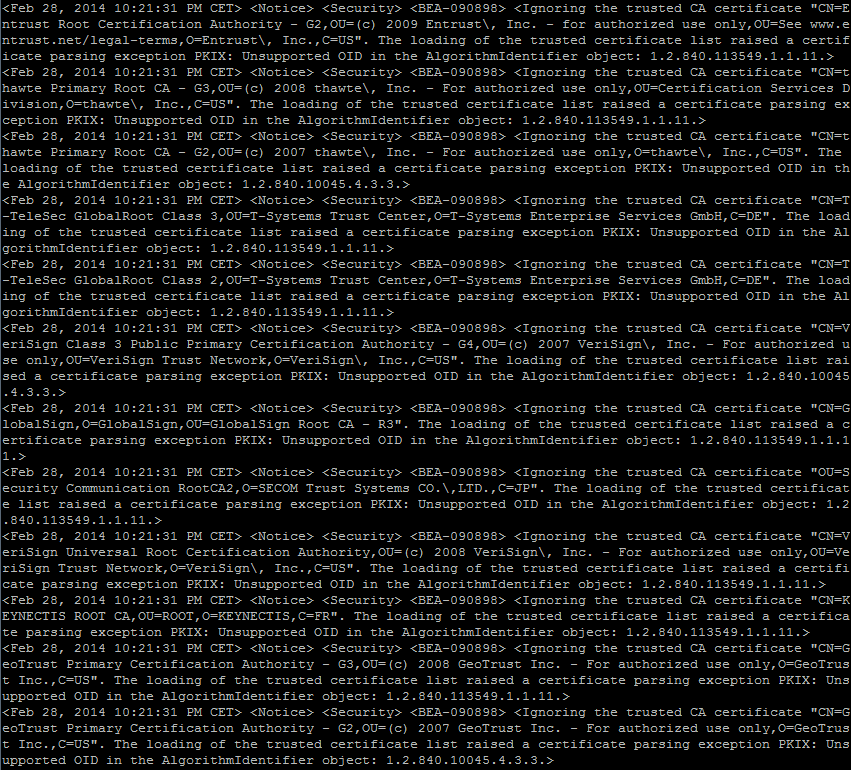
When you use the keystores the log file will show that they are being loaded.
Loading the identity certificate and private key stored under the alias DemoIdentity from the jks keystore file .../DemoIdentity.jks Loading trusted certificates from the jks keystore file .../DemoTrust.jks Loading trusted certificates from the jks keystore file .../cacerts
Since it is demo keystores you will also see at lot of errors.
Creating a Trust Store
You should not use the demo keystores for anything serious. I sometimes encounter customers that use the default Java cacerts keystore. I do not believe this is a good practices. You must also remember to do a backup/restore every time you patch/reinstall Java.
You need a root certificate for your trust store. You can go to the CAs website and download it. This can be a bit tricky since they often supply different types of SSL certificates, and some of them might exist with different expiry dates. If you can access the SSL site via a browser you can export the root certificate. Here is an example from Firefox.
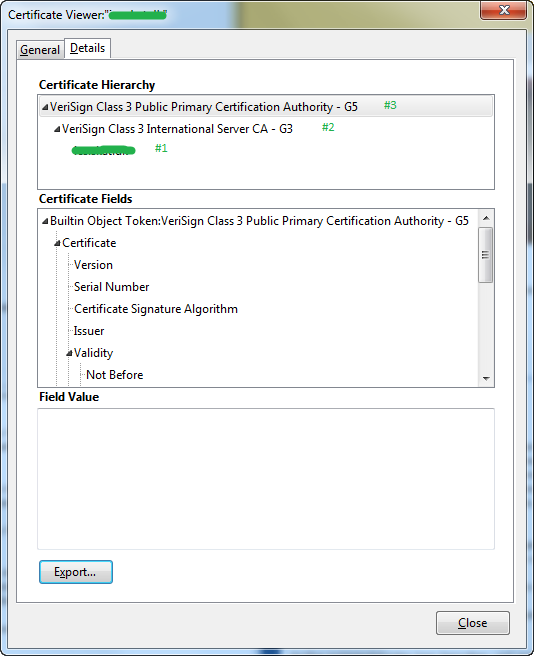
Here you can see all 3 certificates. #1 and #2 was downloaded from the website and #3 extracted form the browsers keystore. Select the root certificate at the top and export it to a PEM file.
Here is an example of creating a trust store. The store type is JKS which is the most used format.
mkdir /u01/app/oracle/domains/myDomain/keystores /u01/app/oracle/product/java_current/bin/keytool -import -v -noprompt -trustcacerts -alias testRoot -file VeriSignClass3PublicPrimaryCertificationAuthority-G5.pem -keystore myTrust.jks -storepass Welcome1
You can list the content of the keystore.
/u01/app/oracle/product/java_current/bin/keytool -list -v -storetype jks -storepass Welcome1 -keystore myTrust.jks | grep "Your keystore contains" /u01/app/oracle/product/java_current/bin/keytool -list -v -storetype jks -storepass Welcome1 -keystore myTrust.jks | grep "Alias name:"
Configure a Trust Store for a Managed Server
You configure Trust stores per WebLogic Server. You have already seen the default setup above. To use a Custom Trust store press the Change button and select Custom Identity and Custom Trust.
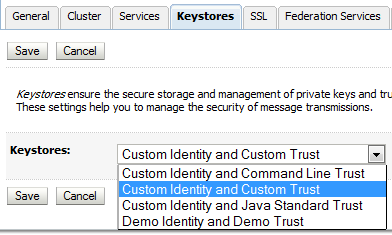
Fill in the Trust keystore information. The case of the store type does not matter.

You do not need an Identity keystore. If you do not use one you will get this error in the log file whenever the WebLogic server loads the keystores.
<Alert> <Security> <BEA-090165> <Cannot find identity keystore file null on server myManagedServer>
If you don’t need a Identity keystore and don’t want this error in your log files you can add an empty keystore.
I normally restart the WebLogic server after changing the keystore information. I am not sure that it is needed though. If you look in the log file you will see the below the first time the keystore is used after it has been changed.
Loading trusted certificates from the jks keystore file .../myTrust.jks
Now everything should be setup and working.
Problems with misconfigured SSL
When you call a SSL protected service, the server should return the SSL server certificate and the intermediate certificate. But this is not always the case. Sometimes the intermediate certificate is missing, the root certificate returned or some other certificate returned.
Here is a couple of recent examples. The first two are missing the intermediate certificate and for the third the root certificate is returned.
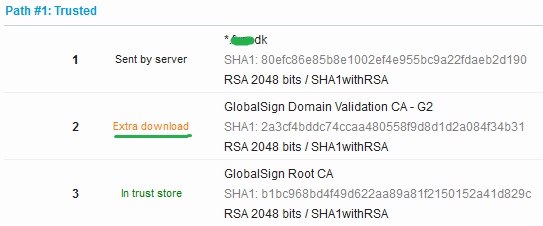
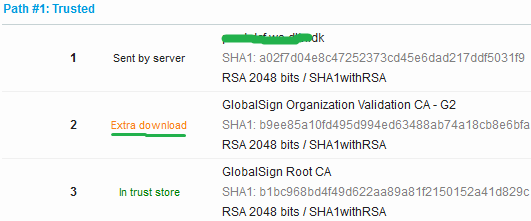
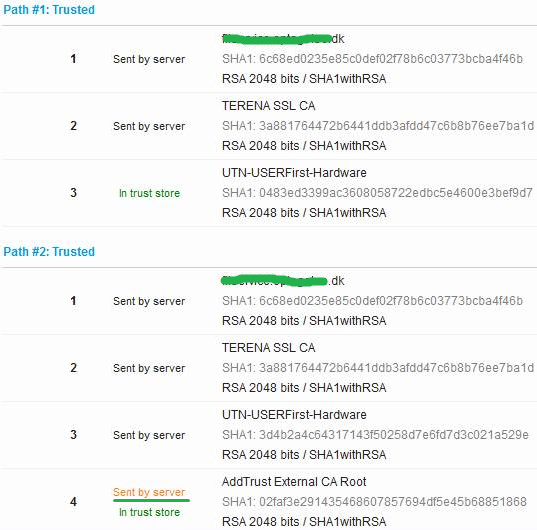
Most browsers can download a missing intermediate certificate directly from the CA and ignores any extra certificates.
The WebLogic server is not so forgiving. I recently had a problem with accessing a web service. I got this error.
<Security> <BEA-090550> <The certificate chain received from mySite.dk contained a V3 CA certificate which indicated a certificate chain path length in the basic constraints that was exceeded.>
The site was returning the root certificate. As soon as this was fixed it worked.
The only thing you can do about this kind of problems is to get the service provider to fix the SSL configuration. To trouble shoot Qualys SSL Labs SSL Server Test tool is very helpful.
Creating an empty Identity Store
As mentioned above you do not need an Identity store, but if you want to avoid the error in the log file you can create an empty keystore and use that.
/u01/app/oracle/product/java_current/bin/keytool -genkey -keystore myIdentity.jks -storepass Welcome1 -alias dummy -dname CN="dummy,C=DK" -keypass changeit /u01/app/oracle/product/java_current/bin/keytool -delete -keystore myIdentity.jks -storepass Welcome1 -alias dummy /u01/app/oracle/product/java_current/bin/keytool -list -v -storetype jks -storepass Welcome1 -keystore myIdentity.jks | grep "Your keystore contains"
If you are going to use an Identity store with real certificates you should try to limit access to it. It should not be owned by same the user that owns the WebLogic installation. If possible it should be owned by the root user and only users that need access should be allowed read access.
 Twitter
Twitter LinkedIn
LinkedIn GitHub
GitHub GoodReads
GoodReads Last.fm
Last.fm
{ 4 comments }
Thank you, that was very helpful.
Many thanks, u saved my time.
Thanks for a valuable information
Hi Peter, that is a very good article and explanation, a great help on this complicated matter.
Comments on this entry are closed.
{ 2 trackbacks }