Here is a quick way of creating your own CA and issue server and client certificates via OpenSSL.
I will test the certificates via the Apache HTTP Server by configuring one and two-way SSL.
I use Oracle Linux 5.
You should of cause only use this for test scenarios.
Install OpenSSL if needed.
yum install openssl
Configuring your CA
mkdir -p /u01/app/myCA/certs mkdir /u01/app/myCA/csr mkdir /u01/app/myCA/newcerts mkdir /u01/app/myCA/private cp /etc/pki/tls/openssl.cnf /u01/app/myCA/. cd /u01/app/myCA echo 00 > serial echo 00 > crlnumber touch index.txt
Change the dir parameter in openssl.cnf to /u01/app/myCA.
Check it.
grep "/u01/app/myCA" openssl.cnf
Create the CA
# Create CA private key openssl genrsa -des3 -passout pass:qwerty -out private/rootCA.key 2048 # Remove passphrase openssl rsa -passin pass:qwerty -in private/rootCA.key -out private/rootCA.key # Create CA self-signed certificate openssl req -config openssl.cnf -new -x509 -subj '/C=DK/L=Aarhus/O=frogger CA/CN=theheat.dk' -days 999 -key private/rootCA.key -out certs/rootCA.crt
Create a SSL Server certificate
# Create private key for the winterfell server openssl genrsa -des3 -passout pass:qwerty -out private/winterfell.key 2048 # Remove passphrase openssl rsa -passin pass:qwerty -in private/winterfell.key -out private/winterfell.key # Create CSR for the winterfell server openssl req -config openssl.cnf -new -subj '/C=DK/L=Aarhus/O=frogger/CN=winterfell' -key private/winterfell.key -out csr/winterfell.csr # Create certificate for the winterfell server openssl ca -batch -config openssl.cnf -days 999 -in csr/winterfell.csr -out certs/winterfell.crt -keyfile private/rootCA.key -cert certs/rootCA.crt -policy policy_anything
Create a SSL Client certificate
# Create private key for a client openssl genrsa -des3 -passout pass:qwerty -out private/client.key 2048 # Remove passphrase openssl rsa -passin pass:qwerty -in private/client.key -out private/client.key # Create CSR for the client. openssl req -config openssl.cnf -new -subj '/C=DK/L=Aarhus/O=frogger/CN=theClient' -key private/client.key -out csr/client.csr # Create client certificate. openssl ca -batch -config openssl.cnf -days 999 -in csr/client.csr -out certs/client.crt -keyfile private/rootCA.key -cert certs/rootCA.crt -policy policy_anything
Export the client certificate to pkcs12
# Export the client certificate to pkcs12 for import in the browser openssl pkcs12 -export -passout pass:qwerty -in certs/client.crt -inkey private/client.key -certfile certs/rootCA.crt -out certs/clientcert.p12
Configure Apache
Install Apache and mod_ssl if needed.
yum install httpd yum install mod_ssl
Edit /etc/httpd/conf/httpd.conf
#Listen 80 ServerName winterfell
Edit /etc/httpd/conf.d/ssl.conf
SSLCertificateFile /u01/app/myCA/certs/winterfell.crt SSLCertificateKeyFile /u01/app/myCA/private/winterfell.key SSLCertificateChainFile /u01/app/myCA/certs/rootCA.crt SSLCACertificateFile /u01/app/myCA/certs/rootCA.crt SSLVerifyClient require SSLVerifyDepth 10
Start the Apache server.
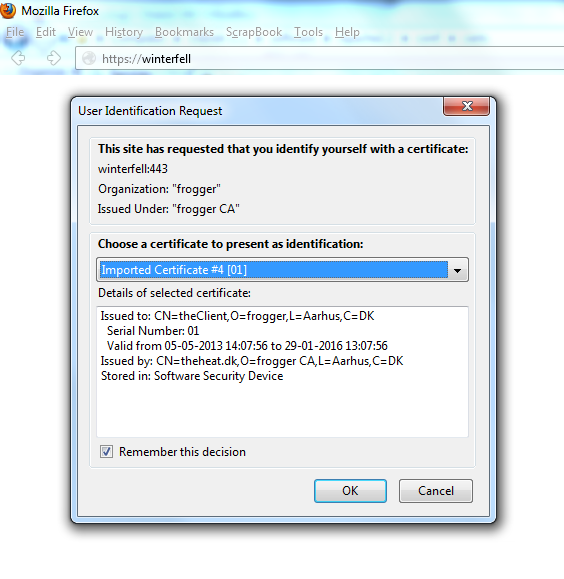
In your browser import rootCA.crt and clientcert.p12.
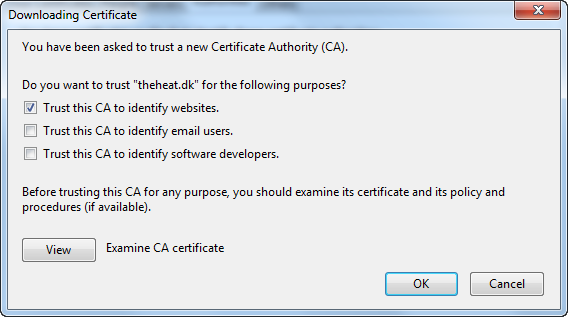
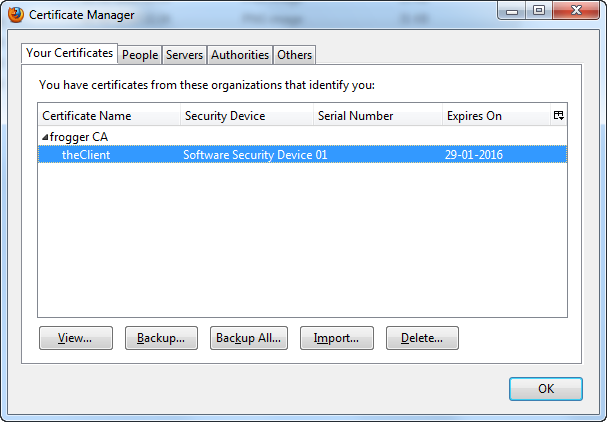
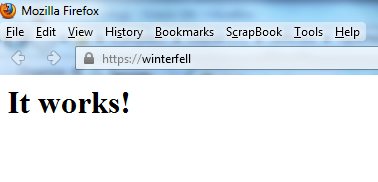
Now it should work.
 Twitter
Twitter LinkedIn
LinkedIn GitHub
GitHub GoodReads
GoodReads Last.fm
Last.fm
{ 13 comments… read them below or add one }
very nice.. it works!
Hi
Very nice work. Concise.
Do you know if you can configure in browser for a given domain to be only verified against your root CA? Just in case a government of a given country ask for a certificate to be signed by their certificate authority of choice to act as man in the middle.
Thanks. Sorry I don’t know.
Hey nice article. Will be doing this for an ocsp responder certificate.
Hey nice article and it works. Can you also let me know how to get it working on IE 8+ or chrome?
You are a life saver!
Thank you for the very helpful article!
Very good. Nice article that gives simple understanding how it works. Now I understand =)
Great article!
It was really helpful and saved a lot of time.
Hi again Peter!
I was trying to renew both the CA and client certificates while keeping backwards compatibility with the previously generated client certificates. So far with no success… Is this possible to do, having executed the method you described?
I would’ve expected it to be a matter of simply generating the CA certificate with the same CA private key… but with a bunch of experimenting, I’ve had no success so far. Any pointers you can give me?
Thanks in advance.
Hi André,
I have never tried that myself, but I would also have expected it to work that way.
Regards Peter
Very nice and useful. Worked perfectly. Thank you !
Thanks for nice article, This is exactly what I was looking for
You are wonderful.
saved my life!